
Hands-On Web Penetration Testing with Metasploit: The subtle art of using Metasploit 5.0 for web application exploitation: Singh, Harpreet, Sharma, Himanshu: 9781789953527: Amazon.com: Books
![How to Hack Exploit Windows Using Metasploit Beginners Guide - HackingPassion.com : root@HackingPassion.com-[~] How to Hack Exploit Windows Using Metasploit Beginners Guide - HackingPassion.com : root@HackingPassion.com-[~]](https://hackingpassion.com/how-to-hack-exploit-windows-using-metasploit-beginners-guide/featured-image.png)
How to Hack Exploit Windows Using Metasploit Beginners Guide - HackingPassion.com : root@HackingPassion.com-[~]
Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 1 (Primer & Overview) « Null Byte :: WonderHowTo





![How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/14-10.png)

![How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/7-40.png)

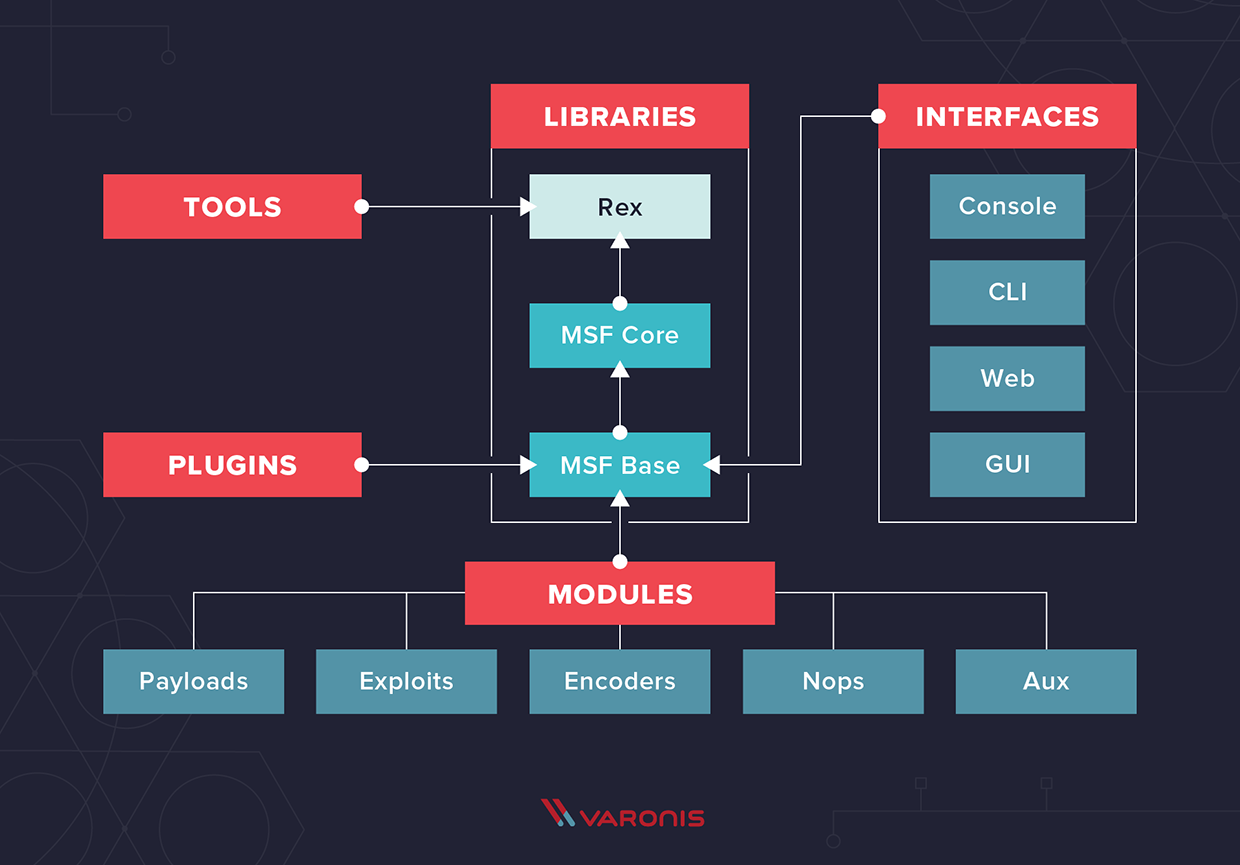

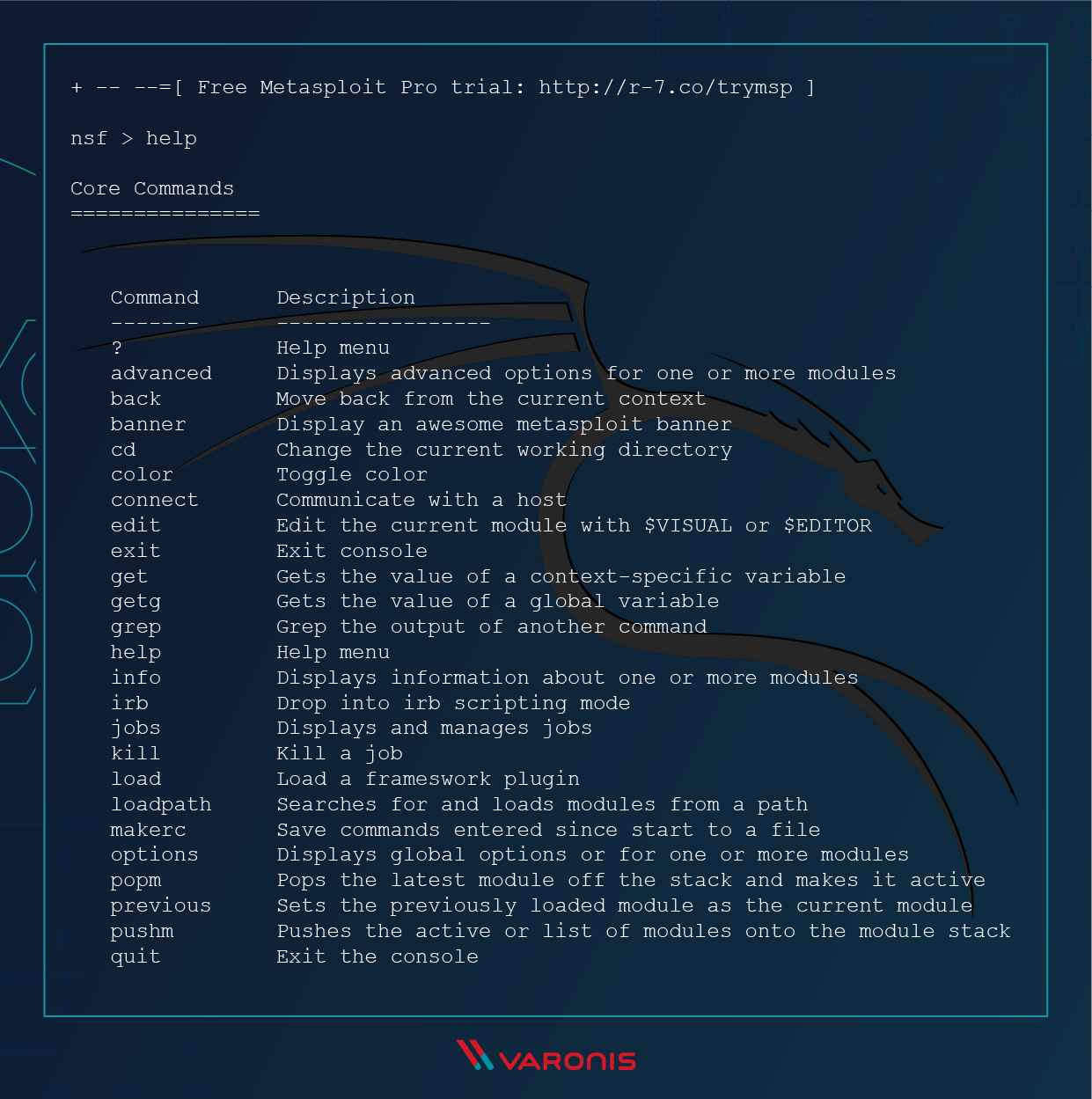
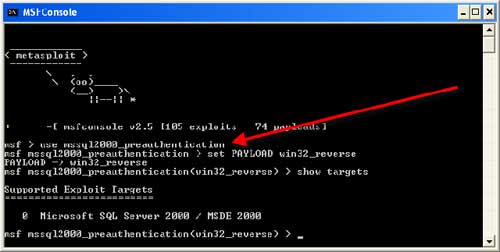
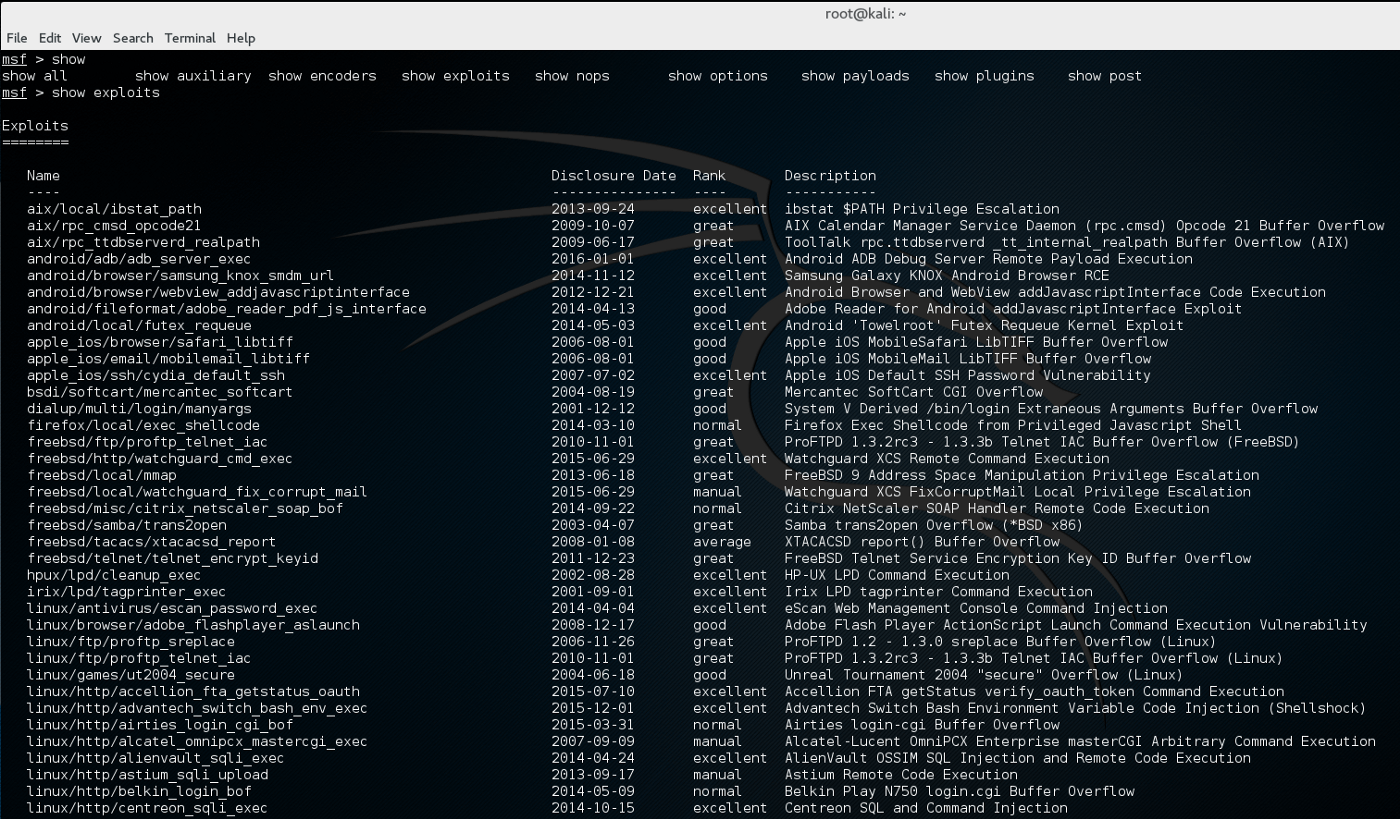
![How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/16-9.png)

![How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/9-23.png)
![How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/5-74.png)

